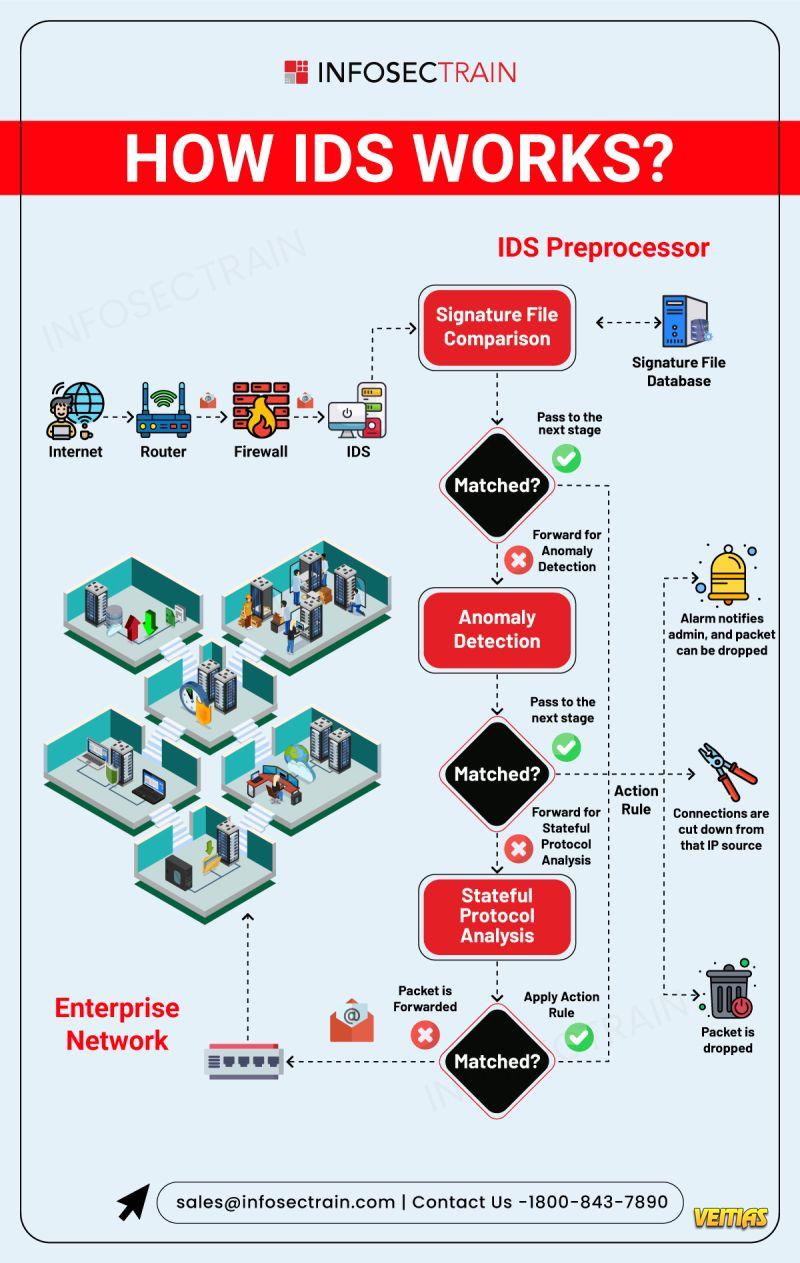
An Intrusion Detection System (IDS) monitors network traffic or system activities to detect suspicious behavior, policy violations, or potential cyberattacks. It analyzes data in real-time using predefined rules, signatures, or behavioral patterns to identify threats like malware, unauthorized access, or data exfiltration. When a threat is detected, the IDS generates alerts to notify administrators for further investigation. While it doesn't block attacks, it plays a critical role in early detection and incident response within an organization’s security infrastructure.
An Intrusion Detection System (IDS) monitors network traffic or system activities to detect suspicious behavior, policy violations, or potential cyberattacks. It analyzes data in real-time using predefined rules, signatures, or behavioral patterns to identify threats like malware, unauthorized access, or data exfiltration. When a threat is detected, the IDS generates alerts to notify administrators for further investigation. While it doesn't block attacks, it plays a critical role in early detection and incident response within an organization’s security infrastructure.
0 التعليقات
0 المشاركات
319 مشاهدة
0 معاينة