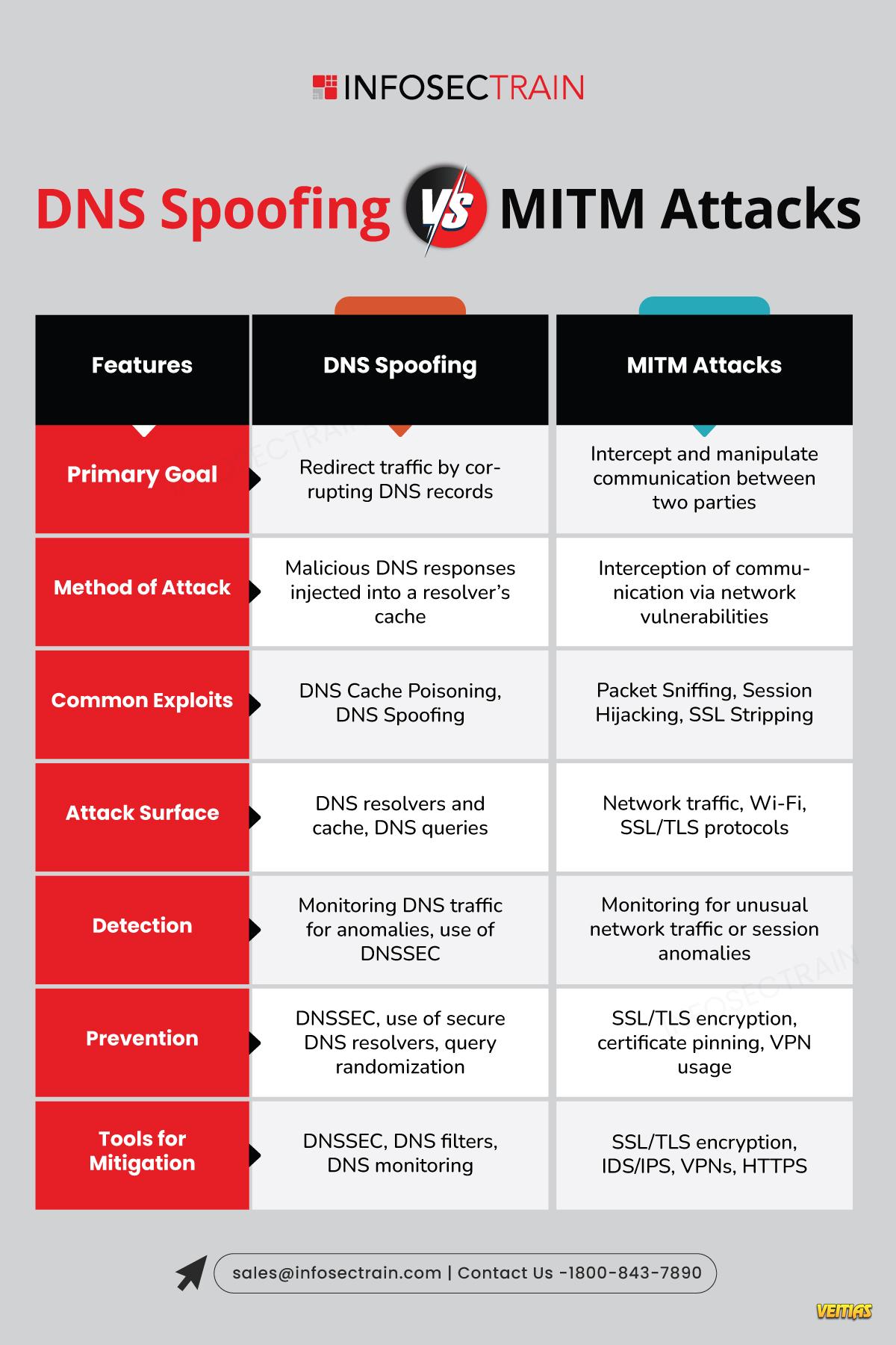
DNS Spoofing vs MITM Attacks: Know the Difference
Understand the key differences between DNS Spoofing and Man-in-the-Middle (MITM) Attacks with this insightful infographic. Learn how attackers exploit vulnerabilities in DNS systems to redirect users or intercept communications to eavesdrop and manipulate data. Discover the risks, methods, and preventive measures to safeguard your network from these common cyber threats. Stay informed and protect your digital assets effectively!
Visit our Site: - https://www.infosectrain.com/
#DNSSpoofing #MITMAttacks #CyberSecurity #InfoSec #NetworkSecurity #PhishingProtection #CyberThreats #ManInTheMiddle #DNSAttacks #DigitalDefense hashtag#TechAwareness #DataIntegrity
Understand the key differences between DNS Spoofing and Man-in-the-Middle (MITM) Attacks with this insightful infographic. Learn how attackers exploit vulnerabilities in DNS systems to redirect users or intercept communications to eavesdrop and manipulate data. Discover the risks, methods, and preventive measures to safeguard your network from these common cyber threats. Stay informed and protect your digital assets effectively!
Visit our Site: - https://www.infosectrain.com/
#DNSSpoofing #MITMAttacks #CyberSecurity #InfoSec #NetworkSecurity #PhishingProtection #CyberThreats #ManInTheMiddle #DNSAttacks #DigitalDefense hashtag#TechAwareness #DataIntegrity
DNS Spoofing vs MITM Attacks: Know the Difference 🌐🔐
Understand the key differences between DNS Spoofing and Man-in-the-Middle (MITM) Attacks with this insightful infographic. Learn how attackers exploit vulnerabilities in DNS systems to redirect users or intercept communications to eavesdrop and manipulate data. Discover the risks, methods, and preventive measures to safeguard your network from these common cyber threats. Stay informed and protect your digital assets effectively!
Visit our Site: - https://www.infosectrain.com/
#DNSSpoofing #MITMAttacks #CyberSecurity #InfoSec #NetworkSecurity #PhishingProtection #CyberThreats #ManInTheMiddle #DNSAttacks #DigitalDefense hashtag#TechAwareness #DataIntegrity
0 Reacties
0 aandelen
1189 Views
0 voorbeeld